This week, broadcasting live from the centre of Cambridge, the Naked Scientists delve into the digital age we live in. We look at new, exciting ways to get kids into coding, how big data is changing the world of healthcare, and we take to skies to go drone racing. But what are the problems we face in this technological age? We find out who is using our online data, and explore the dangers of connecting to public Wi-Fi...
In this episode

01:09 - Getting kids coding: Raspberry pi
Getting kids coding: Raspberry pi
with Eben Upton, Raspberry Pi
Computers, mobiles phones, even calculators - none of these would be possible without coding. But what actually is coding, and is it really a problem that 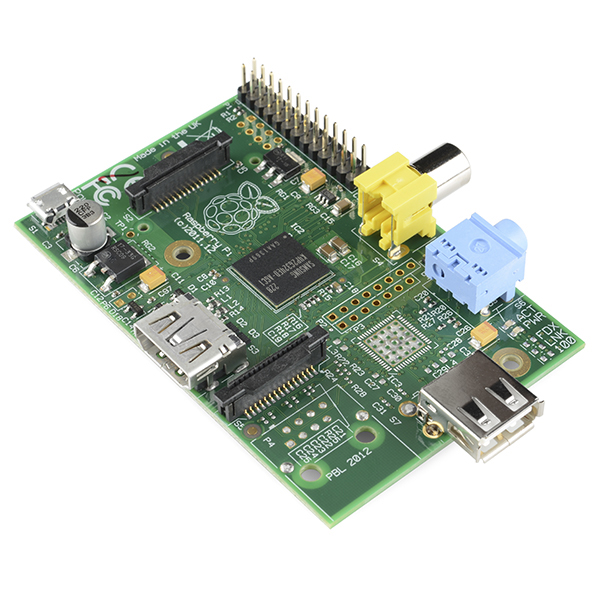 so few of us know how to do it? According to industry figures, over the next 5 years the UK faces a skills shortage of 1.4 million digital professionals; in other words, people trained in computer programming. Someone who is trying to change this Eben Upton, CEO and founder of the Raspberry Pi Foundation, and he explained to Chris Smith how they are planning on doing this...
so few of us know how to do it? According to industry figures, over the next 5 years the UK faces a skills shortage of 1.4 million digital professionals; in other words, people trained in computer programming. Someone who is trying to change this Eben Upton, CEO and founder of the Raspberry Pi Foundation, and he explained to Chris Smith how they are planning on doing this...
Eben - We're trying to get a new generation of children interested in programming computers in the same way we were in the 1980s. Between the mid-1990s and about 2005, we saw a collapse in the number of people applying to study computer science in the university here in Cambridge. It's really been mirrored across the entire university sector in the UK. So big threat to, I guess the future, our future economic competitiveness in the UK.
Chris - Why did you see that collapse?
Eben - We have a hypothesis and that's the disappearance of machines like the BBC microcomputer, the Sinclair spectrum in the 1980s. As those machines disappear, they were replaced by games consoles and the PC machines which are either less programmable or just don't encourage you to programme in the same way. About 10 years after those machines went away, the flow of young people who've been trained on them started to dry up.
Chris - Indeed because we saw this big bubble of people who were born with the BBC coming along. I was one of them. I remember coming to Cambridge to buy my BBC model B plus microcomputer here in Cambridge in 1984. I was a bit of a later comer to the game I understand because it had been out a little while by then. But this really was a game changer because it brought within reach of your average home user the power of a modern computer.
Eben - Yeah, so it provided a computer that sure you could use it to do your school work on, you could use it to play computer games on, and that's why many people bought them. But the thing they all had in common is you turn them on, they go beep and they give you programming problem. The very first thing you could do with all those machines is to start coding.
Chris - What motivated you to actually start Raspberry Pi and to do it the way you've done it?
Eben - I think there's something about a piece of hardware as opposed to just a software platform. A lot of people very early on with Raspberry Pi said, "Why don't you just create an application you could run on a PC?" The nice thing about a piece of hardware, particularly a piece of hardware that a child owns is they can become very, very attached to it. I think the signs are very promising. There has been a massive upswing in interest but yeah, I think it's probably going to be another 5 or 6 years before we really know for sure whether our hypothesis is correct.
Chris - Because you're going to see this sort of lag effect now to see if you've captured this next generation of people and then turn them into computer programmers. I think it's amazing. I mean, let's just describe for people what a Raspberry Pi is. What is it?
Eben - It's a little credit card-sized computer. It's a little credit card-sized circuit board. By default, it doesn't even come with a case but you plug it into your television. You plug a mouse and a keyboard into it and it's a PC. You can use it to watch a video, you can use it to surf the web - a full featured machine. But what we do is we bundle it with every programming language that we think you need to go from knowing nothing about computers to being a professional computer programmer.
Chris - I have to be honest because out of intrigue, having had you on our programme, I went and got one.
Eben - Thank you.
Chris - But it's 23 quid. I mean, that was part of the motivation. Who could ever dream of owning a computer that would cost you 23 quid? I mean, it's incredible value for money really.
Eben - What you're talking about there is our expensive, that's our deluxe model. We actually have a 16-pound model as well. So, it's really about trying to bring it within that - for us, kind of the benchmark here is a school textbook. We know that you can ask children to buy their textbooks at school. Most families can afford it. The families who can't afford it, you can afford to subsidise it. So, it's really getting it into that kind of envelope which is really the driving force behind the design of the hardware.
Chris - I know it works though Eben because having bought one myself, I then felt compelled to do something with it and I immediately, within 6 months, learned two new programming languages. So, there's the evidence. For me, it works but then yesterday, I watched my daughter who I've been encouraging to do this, SSH into using a terminal window into a Raspberry Pi on a Wi-Fi network at home and then actually begin to modify a programme that I'd written and she actually had this little array of things and she could make it print an animal's name as many times as she chose and that kind of thing. I think this is fantastic. You've got someone who's 8 actually speaking computer languages.
Eben - Yeah. There's something wonderful about it. It's something wonderful about the enthusiasm for it. There is always that kind of the other hypothesis, the kind of gloomy hypothesis was that young people, that they aren't interested. They have their tablets and their phones and their games consoles which are very shiny, and exciting, come in a nice box and that that might have killed off the interest. What we actually discovered with the Pi, vast number of kids. If you can get them over that first 5 or 10 minutes, just give them an intro to it then they're away. It gives them a kind of secret knowledge often that the adults - kids love having secret knowledge. When I was a kid, it was being the person who could set the time on the video recorder. Kids love that stuff and coding is a really fertile source of secret knowledge for kids.
Chris - I feel very uneasy that what's been defined as computing has ended up being, "Can I use Microsoft word and excel" and that kind of stuff. The real bare bones of actually, "Can I write computer programmes" has largely been overlooked and lost.
Eben - Yeah. I think we had 10 or 15 years of really, teaching people the wrong stuff. The former unlamented ICT curriculum in the UK was teaching children both things that they didn't find interesting. It was teaching them several times. We meet a child who have been taught how to use PowerPoint every year between the ages of 6 and 18, right? We'd somehow managed to turn computing which could be about writing games and building robots. We turned computing into what was regularly rated as the most boring subject at school. And so, you're teaching these people things. You're boring them out of their minds and the skills you're teaching them are not the high value skills. They're not the skills that will enable them to go and get a high value job. You're basically teaching the outsourceable, offshoreable skills of typing.
Chris - How much will a person who goes into the computer industry earn in a year now? It's quite high, isn't it?
Eben - Yeah. It's one of the best paying professions. If you choose to go into engineering - we're not saying that everyone should. I've been an engineer on my adult life. My view is, I've been paid for 20 years now to play with toys, to basically play with Lego every day. So, some people go into that which I'll find very rewarding. And some people will find that the skills that they've learned by doing computer programming, we think coding makes you a better lawyer. It makes you a better doctor. Maybe it doesn't make you a better novelist but pretty much everything that you might just like to go into as an adult, you'll benefit from that kind of mind set.

07:17 - Sonic Pi: code that funky music!
Sonic Pi: code that funky music!
with Dr Sam Aaron, University of Cambridge
There are hundreds of musical instruments, but would you consider your computer one of them? Sonic Pi is a free programme that can be used on Windows, Mac and Raspberry Pi computers to code music! Sam Aaron composed the program and is now using it to code live music in nightclubs. He took Kat Arney on a tour through the Sonic Pi, to explain how it works and why this can help get kids coding...
one of them? Sonic Pi is a free programme that can be used on Windows, Mac and Raspberry Pi computers to code music! Sam Aaron composed the program and is now using it to code live music in nightclubs. He took Kat Arney on a tour through the Sonic Pi, to explain how it works and why this can help get kids coding...
Sam - I mean, we've just heard about how important it is to get people to code. In my opinion, it's not just about getting people to be professional programmers but also use code to express themselves. In the same way we write and read, we write diaries, we write poems, we could also use code in the same way to express ourselves in really exciting new ways. And so, Sonic Pi is software which allows you to write code, basic words, press a special magic button and hear amazing sounds.
Kat - As a musician, I'm really excited by this and I know a lot of computer musicians, they're using programs like Ableton and things like that that cost hundreds and hundreds of pounds to make music and often, I play with them. So, how is this different? Why did you make this? I mean, I downloaded it earlier for free.
Sam - Absolutely. So, you heard Eben earlier talking about lowering the barrier to entry. I mean, part of the deal about the Raspberry Pi, it's extremely affordable. And so, the software I've written is also extremely affordable. It's entirely free. And so, the idea is, if you don't have any money, it doesn't matter. You can use the software. Also, it runs on all computers. It runs on a Raspberry Pi, but also runs on a Windows or a Mac. So, if you already have a computer, use that, but if you don't, then get one of these Raspberry Pis because they're really wicked fun.
Kat - Now, is this just a way of basically tricking kids and tricking even adults into doing a bit of coding or is it actually genuinely a musical tool? Could you make musical compositions that would stand up on this?
Sam - I mean, is writing poetry tricking kids into grammar? Right? Clearly not, right? So, this is not tricking people into making code.
Kat - Maybe a little bit.
Sam - Code is an amazing expressive form and it's just shown people that potential. And yes, Sonic Pi is a new musical instrument that you can use today to perform in nightclubs and venues to make music and it's a lot of fun.
Kat - Right. Well, enough talking about it. Let's see it. So, we've got a computer screen up. We got a little Raspberry Pi sort of naked circuit boards sitting there. And on the screen, I can see just some lines and lines, and lines of code. They look like words, sleep, bit, crusher, soul, sustain. What is this?
Sam - Yes. So, I'm showing you here one of the examples. So, when you start up Sonic Pi, you have a help system. The help system contains a bunch of examples. This is one of the pre-canned examples just to show you what you can do with the system. So, shall we hear it?
Kat - Yeah. Let's play something.
Sam - Let's give it a go.
(music)
Sam - So we're getting some of that dance music. This is all generated in real time on the Raspberry Pi using lots of fancy mathematics to make the sounds. The synthesisers are all real time generated. So, this little Raspberry Pi is an extremely capable machine, it's able to do this. So, I use the same system to perform on stage at night clubs.
Kat - That is incredible. It's kind of pumping. We're all like, "Come on. Hands on the air people!"
Sam - They're going wild.
Kat - Reach for the lasers.
Sam - Calm down people! Calm down!
Kat - Never thought I'd say on the radio. So, what have we got going on here? So it's making drums and synths and all sorts of things.
Sam - Absolutely. So, shall I show you how to get started?
Kat - Okay, let's have a go. Let's make a tune, banging tune.
Sam - So, the first word to learn in Sonic Pi is the word play because we're playing a note, but also playing. We're having fun, right? So I write the word 'play' and then I choose a number to play. Let's choose 80. We hear a little beep. That's it. That's your first programme. How easy is that to write?
Kat - Yeah, that was, even I, I think. As the kind of notes, a paper musician could do that
Sam - So, once you write your first programme, the next thing is how to change these things. So now, we can change this number 80 because numbers can go up and down. Notes can also go up and down. So, if I chose a lower number like 60, you get a low note, right?
Kat - Yes. It's much lower, okay.
Sam - If I'd said 90 I'd get a higher note, right? So, done. So now, we can play all the notes we can imagine then we need a way to make a melody. So, if I play note 60 then I need to have a way of saying, "Well, wait for a bit. Let's sleep for a second and then play another note. Play 65, say and then let's sleep for half a second and play 72." So this way, we're able to play different notes and make a little melody, right?
Kat - I like that.
Sam - At this point, with these two commands, 'play' and 'sleep', we can play pretty much all western notation. So, if you take any Bach, or Mozart, or Beethoven with two commands, you can reproduce those things. It's not slamming beats yet, but we've already done classical music.
Kat - Okay. Can we make it a bit more funky? Can we get it kind of going?
Sam - So, the next thing we do is once you got playing, we need some programming structures to help us to manipulate this stuff. So, I've invented something called the live loop. A live loop is just a thing which can loop. So, let's play a sample loop Amen which is Amen Break.
Kat - Is that the Amen Break? Very well known.
Sam - Sleep for the one length of that sample.
Kat - That's what drum and bass is made of fans.
Sam - And now we've got this loop going around, but whilst it's playing, I can now change the rate, say to be half, and now, we got it half and I can bring it back up to 1 again. I'm just changing one number here. Let's go reverse, minus one. Let's add some bass and then let's add some slicer to slice the volume in and out. So, I just choose where to start the slicer, where to end it. And so, just by adding a simple piece of code on top of another simple piece of code.
Kat - I think we've got a number one hit here already. I mean, it's fairly boring and repetitive, but there you go.
Sam - That's what dance music is.
Kat - Exactly.
Sam - You have to be able to dance to it. So, you say it's fairly boring and repetitive, but we've only got 9 lines of code here.
Kat - How long would it take someone like me to actually make a tune, a kind of a song with a beginning, a middle, an end, some structure?
Sam - It depends on how complicated the tune would be. I went to a school in New Castle, Benton Park Primary School where they have a Sonic Pi Orchestra and they've been teaching themselves, the kids have been teaching themselves. And the primary school kids have been teaching their local teachers how to do the stuff. This is 10-year olds. Okay, so you just need some time and some creativity and some fun and some patience. In a few days, you can get the basics down and then depending on how much time you want to put into it, in the same if you want to learn a violin, how much practice you put into it, you can get to do some wicked things pretty quickly.
Kat - Is there transferable skills from learning to write these kind of stuff?
Sam - Absolutely! This system is written in the same language that Twitter was originally written in.
Kat - And that's boring and repetitive.
Sam - Using exactly the same structures as Twitter was originally written in. All the UK government work is all written in the same language. This language called Ruby.
Kat - Also boring and repetitive.
Sam - Absolutely transferable. But code is not boring. It can be repetitive, but the computer does the repetition, not you.
Kat - So, we're going to have a little bit of time now. I want you to show me what you can do because you play in night clubs, don't you? You've played this stuff out and people do dance to it.
Sam - Absolutely, yes. So, let's choose one of the examples in a way to start. So, this is an example called ("Tilburg")(music playing). So, this is going and so, I've got my basic tune around. It's very hard to play that. I can't fully hear myself. Normally, these beats are bashing out. So, I can turn the randomization off.
Kat - I do like my house music and this sounds pretty good.
Sam - It's nice, yeah. I start and stop it. Sorry, I made a mistake. So, you can make mistakes all the time. It's totally fine. So turn off bits, turn of the bass drum and then get the rhythm going again, and then drop a kick in again. Now, off we go. So, all I'm doing there is editing some very simple lines to make that happen.

15:03 - Recreating a computer from history
Recreating a computer from history
with Dr Nigel Bennee, Physicist
How much of your day is spent on a computer, looking at your phone or doing something online. It's easy to forget that just 60 years ago none of this was possible, and by today's standards the simplest calculations took weeks of combined work from people. That is, until something called EDSAC came along. EDSAC stands for Electronic Delay Storage Automatic Calculator, and was built at Cambridge University shortly after the second world war to start crunching through these complex maths problems in a much less time and 1000 times more quickly. It was the first computer built for other people to solve problems on. Today, virtually nothing of EDSAC survives, but now a team are attempting to build a working replica, to eventually put on display in the National Museum of Computing at Bletchley park. Nigel Bennée is a retired physicist building a section in his garage in Cambridge! Graihagh Jackson went to meet man and machine to for a cup of tea and a trip through history.
something online. It's easy to forget that just 60 years ago none of this was possible, and by today's standards the simplest calculations took weeks of combined work from people. That is, until something called EDSAC came along. EDSAC stands for Electronic Delay Storage Automatic Calculator, and was built at Cambridge University shortly after the second world war to start crunching through these complex maths problems in a much less time and 1000 times more quickly. It was the first computer built for other people to solve problems on. Today, virtually nothing of EDSAC survives, but now a team are attempting to build a working replica, to eventually put on display in the National Museum of Computing at Bletchley park. Nigel Bennée is a retired physicist building a section in his garage in Cambridge! Graihagh Jackson went to meet man and machine to for a cup of tea and a trip through history.
Nigel - Immediately after the war, Maurice Wilkes, he'd worked on radar. In radar, they had managed to get a storage device where you could store the equivalent of 72 bytes in a 5 foot tube full of mercury.
Graihagh - I mean, that's not even a Word document, is it?
Nigel - It's barely a character. You might get a tiny little icon. So, the biggest constraint to making a computer was, where can we store it? EDSAC had the largest memory that existed. They had about half a ton of mercury.
Graihagh - Which equates to how many bytes?
Nigel - 2,300 bytes.
Graihagh - It still doesn't sound that much.
Nigel - And that was the entire machine to hold all the programme, and all the data that you were going to execute.
Graihagh - It wasn't just important in terms of memory. My understanding is that lots of scientists are running lots of mathematical equations and women were taking months to do them. So, it played a pretty fundamental role in science as well, once it was built.
Nigel - Absolutely. EDSAC claimed 3 Nobel Prizes and the ladies you refer to were known collectively as computers because they computed. They had turn a handle calculator where you put the numbers on the thing, turn the handle, very elegant, but very, very slow. To put it in context, EDSAC runs at about 1500 times faster than one of those ladies would do.
Graihagh - Can we go and see it because I know you've got your own workshop dedicated to replicating it?
Nigel - Yes, let's go and see it. What you can see here is about 25 per cent of the EDSAC replica. There's three 7-foot high steel racks painted in nasty yellow colour. That's because they're in a film. The Imitation Game. These 3 racks represent the actual calculator part of the computer. A lot of the rest of the machine is to do with memory.
Graihagh - What I would describe what I'm looking at is, what looks like a series of almost bookshelves. And on each shelf, there is hundreds of metal tubes, some painted bright red, almost like a lipstick and this is just all various instrumentation to do maths like the modern day calculator, what it might have on my phone.
Nigel - Absolutely.
Graihagh - Take me through what would've happened back in the 1950s. I'm a scientist. I'd like to do - not my 2 times table, but I'd like to do something a bit more sophisticated than that. How would it work if it was in its full glory here?
Nigel - So you were - I forgot the two guys' names. They both won Nobel Prizes, but they were trying to work out how nerve pulses propagated through nerves. Their theory involved a complicated balance or imbalance of chemicals going on and these can be represented by differential equations.
Graihagh - Okay, so I've got my equation now and you didn't have a lovely keyboard. How would you translate that into EDSAC?
Nigel - You would type a paper tape.
Graihagh - Sorry, paper tape?
Nigel - Let me show you some paper tape. This is the box here. It contains paper tape. That is programme 17 and the date is 1968.
Graihagh - It's almost like braille but instead of being a bump, you've hole punched it through.
Nigel - Yes. That goes into the computer and then you'll have another tape where you've typed data in that you need to analyse.
Graihagh - So, that goes into the machine. The machine does some magical maths I assume.
Nigel - Well, the maths actually isn't really so magical. The key thing about computers is they very rarely do anything complicated but they do complicated things by doing simple instructions, lots of them.
Graihagh - Given that lots of people are reconstructing EDSAC. I wonder what happened to it in the first place.
Nigel - It was very unceremoniously dismantled and sold off as scrap metal. Some people did actually take them away as bookshelves.
Graihagh - Someone at home has got EDSAC as their book shelf. Why are you going about completely reconstructing it?
Nigel - Before digital computers existed, there was no need to programme because no one had the concept. Once they existed as Maurice Wilkes said, "Now, we've got EDSAC. Now, we need to learn how to use it. i.e how to programme it." Well, that was the beginning of software so that makes it very important. The second motive for it is the education value. When school children come to the museum, beforehand, they will be able to write programmes for EDSAC and when they come to the museum, it will run their programme, print out a result, and they can take that home with them. They will be programming at the nuts and bolts level of computing. That's incredibly important.
Graihagh - I think especially since so many people are out of touch with - I mean, I certainly have no idea how my computer works yet I rely on it day in, day out.
Nigel - You don't need to. My view is that in the 21st century, computer literacy is as important as learning to read and write, and do arithmetic.

21:45 - Introducing the BBC micro:bit
Introducing the BBC micro:bit
with Gary Atkinson and Tristan Hughes, ARM
In October this year, every 11 year old in the UK will receive, via their school, a  free gadget called a micro:bit. It's been developed by a group of collaborating organisations, led by the BBC, including the Cambridge-based company ARM. ARM design about 99% of the world's microchips that you find in mobile devices, like smartphones. Gary Atkinson and Tristan Hughes work for ARM and they unveiled the new Micro:bit for Chris Smith...
free gadget called a micro:bit. It's been developed by a group of collaborating organisations, led by the BBC, including the Cambridge-based company ARM. ARM design about 99% of the world's microchips that you find in mobile devices, like smartphones. Gary Atkinson and Tristan Hughes work for ARM and they unveiled the new Micro:bit for Chris Smith...
Gary - The micro:bit is a very small pocket-size computer but it differs from the Raspberry Pi in that this is the sort of platform that you'd find in a smart watch or a wearable type device, you know an internet-of-things type device.
Chris - It's sort of roughly the same size if I snapped my credit card in half which I feel like doing it judging by the bill at the moment. It would be about that big.
Gary - Yeah. It's about the - I'm showing my age talking about matchboxes, but it's about the size of a matchbox. So, it's got an array of LEDs on the front. So you can have scrolling text, you can have little sprite type designs. It's got a couple of programmable buttons on the front. Similarly to the Raspberry Pi, one of the things that kids really are interested in is the fact that this is not covered in a box, that you can actually see the different chips and the pieces. And so, on the back of the micro:bit, we describe where the Bluetooth low energy antenna is and where the USB chip is, and where different pieces are so they can actually have a look and see what things are called.
Chris - This is a PCB, Printed Circuit Board and I can see all of the tiny little tracks which are the connections between the things. So, what could I do with it?
Gary - As it stands by itself with a battery power supply, there is an accelerometer so it knows when it's being moved. It has a magnetometer on board so it knows what direction it's pointing in.
Chris - Like a compass.
Gary - Like a digital compass. You can create little games, you can scroll texts, you can use it as a controller. It has Bluetooth low energy built into it so you can connect it to your mobile phone. So, it can pull data from the phone like GPS for example if you wanted location based algorithm to run, or you could use it as a little hand-held controller for a game running on an android phone for example.
Chris - But critically, it doesn't have a keyboard or anything like that so how do you get your programmes or whatever you want to do with it into it in the first place?
Gary - You can either connect it via - there's a micro USB port so you can connect it to a PC. You can go to the micro:bit website and you can log in and you can choose your development environment from a simple GUI type platform like...
Chris - It's a Graphical User Interface for those not in the know of this text-speak Gary.
Gary - Graphical User Interface, so like scratch called blockly or you can use java script or python or C++, depending on your preference or your confidence level. And that's all browser based so you can do that on a PC or a laptop or a tablet, or a mobile phone. But the difference here is, once you may be doing that via USB, you could also, because it talks bluetooth to your tablet or your phone, you could actually programme it and we can flash this device over Bluetooth. So, over the air. So you could imagine kids on the bus sending messages to each other and in real time, changing that message and recoding the device.
Chris - Sounds perfect for a Naked Scientist, something you can flash. Let's come over to Tristan Hughes because you have got an intriguing setup here, Tristan. A giant watering can and beautiful looking orchid in a pot.
Tristan - Yes, we have. This is our automated plant watering system demonstration. So, it's a very basic demonstration using the Micro Bit. So you connect it up to a moisture sensor that's currently sat in the plant. So, that's telling us how moist the soil is around the plant. We've also connected up, inside the watering can, we've got a small pump and that's also connected to the Micro Bit. So, when the Micro Bit senses that the soil is getting a bit dry on the plant, we can use that to turn the pump on and water the plant.
Chris - Can we see it work so we actually know that this really is actually doing what it says on the tin?
Tristan - We can. So, if we remove the moisture sensor out of the soil for time being to pretend that it's gone really dry...
Chris - Wow! You can probably hear this at home. The watering can is issuing a big jet of water and it's filling the pot up. The moisture sensor is quite literally two bits of metal. So, you're just detecting the ability for electricity to pass between the two.
Tristan - Yes, we are. So, that just gives us an analogue voltage into the Micro Bit and then when we code the micro:bit, we can just say, is it higher than a certain voltage or lower? And that's how we're using it to determine that whether to turn the pump on and off.
Chris - So, if a child wanted to do that at home, how hard would it be?
Tristan - It's fairly simple. You just connect the moisture sensor up to the micro:bit using one of the inputs across the bottom and the code is very simple, using the tools that have been provided to enable this kind of application to be produced.
Chris - So, this goes back to what Eben was saying earlier. It's all about empowering kids to get hands on and do something. Let me ask you then Gary, why did you get into computing in the first place and then end up ultimately working for what is ostensibly one of the world's most important tech companies?
Gary - Well, similarly to Eben, I'm a child of the BBC micro. When I was at secondary school, we had one in the classroom. Some people took to it very naturally, some people didn't. I probably didn't actually, but we were all exposed to it and that's similarly the rationale for what we're doing with the micro:bit, we're giving this to everybody, state school, private school, home school, every year 11 child in October. We want it to be completely inclusive. It didn't matter - male or female, ethnicity, social background - you get one. The goal is, assuming that we can repeat this every year that we may be getting another 100,000 engineers who are interested either in STEM or RICT but just creatively using electronics to do something interesting.
Chris - Let's hope it works because as we said earlier, we need 1.4 million of them. So Tristan, apart from watering plants, what else have you got dreamed up for this thing that people could conceive of doing with it?
Tristan - So, we've also done a hoodie that has LED stitching around the hood. But it uses the Bluetooth low energy on the micro:bit. So, you have a smartphone app and you can set the colour of the LEDs on the hood using that. We're also thinking about different ways we can use the sensors on-board the Micro Bit so you can create something just using the Micro Bit alone without having to connect any external sensors to it.
Chris - Alarm for my bedroom perhaps?
Tristan - Definitely, yes. With maybe a methods so that it can text you so you know that when someone has entered your room.
Chris - Really? That could be quite cool. So, how would you do that?
Tristan - Again, you could use the Bluetooth low energy on the micro:bit to connect to your mobile phone and use that as a method of notifying you when something like that has happened.
Chris - Who was invading your bedroom. Well, we wish you luck with it. Thank you very much. So, the launch is in October across the country, but it's being unveiled this week, Gary.
Gary - Yeah. It was unveiled on Tuesday just gone in London. The teachers will be getting theirs in September and then all the kids should be getting theirs in October.

28:53 - Ready, Set, Drone!
Ready, Set, Drone!
with Simon Vans-Colina, London Hackspace
With current technology the sky really is the limit - and advances in software and  downsizing computer chips have allowed drones to really "take off". Drones are unmanned aerial vehicles, which can be flown autonomously, or via remote control from the ground. Drones are now so cheap to make and build that they can be owned by just about anyone - and with these fast little flying copters a new sport has been born: drone racing. Georgia Mills went to see a man about a drone: Simon Vans-Colina is one of the founders of the London Aerospace Group and also a drone pilot...
downsizing computer chips have allowed drones to really "take off". Drones are unmanned aerial vehicles, which can be flown autonomously, or via remote control from the ground. Drones are now so cheap to make and build that they can be owned by just about anyone - and with these fast little flying copters a new sport has been born: drone racing. Georgia Mills went to see a man about a drone: Simon Vans-Colina is one of the founders of the London Aerospace Group and also a drone pilot...
Simon - Drones themselves, as a thing that you can buy, a commercial product are only a few years old. But as mobile phone technology made chips available that are fast and good accelerometers, that's made possible smaller and smaller drones. At some point about 2 years ago, people realised that you could build these small carbon fibre drones with good quality lithium-polymer batteries and they were really, really fast, and then people just started racing them.
Georgia - How did you get into racing?
Simon - I saw a video on YouTube when I was snowboarding once and somebody just like absolutely flying through the trees and it reminded me of Star Wars, the pod racing or like flying speeders through the forest and I was like, "I just have to do that." So, I think I ordered all of the bits on that first weekend and then built my first one.
Georgia - How do you go about building a drone?
Simon - You watch a lot of YouTube videos. Everybody who flies drones at the moment also builds them. There aren't really any off the shelf, ready to buy racing drones yet, although they're coming. Even if you buy one off the shelf, the first time you crash it, you're going to have to rebuilt it and crashing and rebuilding is part of the hobby or part of the sport so far.
Georgia - Is there any element of software to it?
Simon - The drones will have a little computer chip called a flight controller. That runs an algorithm called the PID loop and there's a few different implementations of the PID loop. The one that we all fly is called cleanflight. It's built by a British programmer called Dominic Clifton. So yeah, you can download the source code for this. They're all open source. If you know programming, if you know a little bit of C, you can download the source code and just hack on it and make it do what you want.
Georgia - I see you've got some here laid out on this table. There are a variety of sizes, all of them have 4 sticky-outy propellers on them. Can you tell me a bit about these guys?
Simon - This is the Thug 180. It's made by thug frames. This one here, I call The Nerd because I kind of designed it myself and it looks like it's got glasses on and the camera in the front of it is the nerd-cam.
Georgia - The Nerd is the one that can see in 3D. I'm quite excited to see one of these in the air. Can we have a go?
Simon - Yup, let's do it. So, you'll put these goggles on here.
Georgia - What are these goggles for?
Simon - This receive the picture from the drone so you see what the drone sees.
Georgia - Wow! So we get a drone's eye view of the flight.
Simon - Yup, exactly.
Georgia - And I see you've got a spare. So you're going to take me along for a ride.
Simon - Yup, absolutely. So, you'll see the same thing that I'm seeing.
Georgia - Oh wow, that's so weird! So, I'm can see myself through The Nerd vision, as it were, with the goggles.
Simon - So, what I'm going to do is, I'm going to fly for you now and you can just sit back and enjoy the 3D vision.
Georgia - So we're just hovering in the air now, taking a look at - it's looking at Simon as he's got the controller and going really low. You can see almost each blade of grass coming towards you. This is quite frightening. I wouldn't recommend doing this on an empty stomach to be honest. Can I trust that you're not going to fly this thing into me? It's coming very close. Almost felt the breeze there as it flew past. Really picking up speed now, zooming along the ground. Oh! It had a 3D crash. Let's go and see if it's okay. Is it alright?
Simon - Hit the grass and rolled.
Georgia - Avatar's got nothing on this. A live 3D drone crash - it's amazing!
Simon - Yeah.
Georgia - When is drone racing going to be in the Olympics?
Simon - Soon, I hope. It's so much fun. There are so many leagues starting up. There's a big one in the US called the Drone Nationals which is bringing together the best pilots in the world and it's an amazing spectator sport too because everybody brings their goggles and everybody watches everybody else's race from the first person. So, it's like - imagine going to the Formula One races, but everybody can see the view from the driver's cockpit the whole time. So, it's really fun.
Georgia - Is it all fun and games with these drones? Are there any other applications people have been looking into?
Simon - We know people that are putting infrared cameras on drones to do search and rescue, so if there was somebody, a hiker, lost in the forest. Amazon is talking about using drones to do deliveries. I personally can't see how that's going to work. I don't think it's going to work in London. It's very hard to find somewhere you can safely drop a package off in London.
Georgia - Is there any chance that people could hack in to drones?
Simon - Sure, absolutely. I mean, I saw a tweet the other day that one day, we'll see a news drone chasing a police drone that's chasing a pirate drone that ripped off an amazon drone. Like we use frequency hopping an encrypted radio already so that we don't have to worry about people taking over our drones. But our video signals are still analogue. When we're flying, anybody can pick up our video signals.
Georgia - I was in very competent hands when we flew around but say, I don't know, someone who'd had a bit to drink when they're flying and there's nothing...
Simon - You don't drink and drone. It's one of the rules.
Georgia - Well, there's nothing to stop a nefarious or drunk person flying into someone or even just spying through someone's window.
Simon - People always say like, "Are you worried about people using drones to spy on people?" but my drones have never snuck up on anybody. They're so loud and they're so obviously in the air. There's a great device that's been invented that protects people from being spied on by drones. It's called curtains. So yeah, I don't think that's a real issue. I think that being hit on the head by a half kilo flying brick with spinning blades on the front is more of an issue than being spied on by something that's really, really loud and obvious. There are risks to them and it's a pretty unregulated industry or pretty unregulated hobby right now and everybody is very, very careful to make sure that we only do it safely and stuff, but like society is going to have to adapt.
Georgia - So, can you program a drone?
Simon - Yeah. So, there's a piece of software called NodeCopter which lets you send commands to the drone using the same programme and language they use on the web. So, if you know Javascript, you can basically programme a NodeCopter to take off, hover, turn right, turn left. It doesn't give it the sort machine vision, obstacle avoidance, or way pointing or anything like that. But for just like really basic controls, you can have a computer control a drone really easily.
Georgia - I saw a video on YouTube of someone I think they had coded it to follow red and someone was running around with a red flag and the drone was chasing them. Is that possible?
Simon - Yeah, absolutely. But the thing is, the image recognition stuff, you have to send a video back to a computer at the moment. As computers get faster, we're hoping to move more and more of those smart algorithms onto the microprocessor on the drone which will make them a lot more autonomous. If Moore's Law keeps holding and microprocessors get faster, we'll be able to move all sorts of interesting algorithms onto the drone. Like all of those crazy things like image recognition and face recognition and like following a particular car and all of that stuff will be able to be done on the drone once the processors are fast enough.

36:11 - Using big data to improve healthcare
Using big data to improve healthcare
with Dr Lydia Drumright, University of Cambridge
In October last year Addenbrooke's Hospital in Cambridge became the UK's first to become an 'e-hospital' and transfer patient records from offline paper copies, to online records, meaning staff can now access records even on mobile devices around the hospital and even from home when they are on call. Lydia Drumright is a lecturer in Clinical Informatics based at Addenbrooke's, and she explained why the hospital made this move to Chris Smith...
become an 'e-hospital' and transfer patient records from offline paper copies, to online records, meaning staff can now access records even on mobile devices around the hospital and even from home when they are on call. Lydia Drumright is a lecturer in Clinical Informatics based at Addenbrooke's, and she explained why the hospital made this move to Chris Smith...
Lydia - It's about universal, high quality care for all and that's really the focus that Addenbrooke's Hospital has.
Chris - What does actually making an eHospital, an electronic hospital, involve?
Lydia - So, what it involves is taking what we used to see as paper records and we had paper records and electronic systems as you well know. In the laboratory, we had electronic systems and we had a bit a paper and everyone had to go on different systems. This is about taking all the paper, all the electronic systems and universalising them into one. So, what that means is that when you're the medical doctor as you well know, for any given patient at any given time of the day, you have 100 per cent of their medical information up-to-date right in front of you when you need it.
Chris - It sounds pretty simple though because to be fair, I can do online banking from anywhere in the world. I can move some money around on some bank accounts. Why is this a challenge when it comes to health?
Lydia - There are a number of reasons that it's a challenge. The first being, if you haven't done it before, we took everything that every doctor, nurse, and other care provider knew in the hospital and changed it on them overnight. They had to change the way they worked and the way they operated. That being said, they're working very well with it now and very pleased with it for the most part.
Chris - Where will this return benefits in healthcare?
Lydia - So, what we've done as part of Cambridge University Hospitals Foundation Trust is combine this with research and that's always been the plan from the beginning. CUH has the opportunity and the relationship with the University of Cambridge to do this and be the cutting edge so we can deliver high quality translational research. I think you and I were having a discussion before, talking about just some of the things that can happen. And out in Stanford, they talked about really important items where, when a drug goes out to market, we think it's safe, we've tried it out, but we don't know until it's been out on the market for 10, 20 years, and we don't know what the side effects will be. But we can monitor those when we are using an electronic medical record system.
Chris - Is that because rather than having to pay a human to relentlessly plough through many, many, many hospital notes, read appalling handwriting and try to work out what is wrong with the patient, what's happened to a patient, what drugs they've been taking, and all that takes time, you could write a computer program which would do that very, very quickly on a massive scale.
Lydia - Absolutely. Our team is doing that now at Cambridge University Hospital and you can also, knowing about reading medical notes - just to go back to that - and patient safety, I've been through many, many of them in my career as researcher. I think it's hard for ourselves or even other doctors to read another doctor's handwriting in the notes. Everything is clear with...
Chris - It's intentional, Lydia.
Lydia - I can't comment on that, Chris. Maybe you can.
Chris - So, what you're saying is, because we can marshal lots of data from lots of people very quickly, a) we can make new discoveries about how drugs work, about how drugs work even better under certain circumstances, but equally, we can make things safer because we can find out when things don't work so well, because we can link up and look at lots and lots of people and you've got to look at lots of people to get lots of data to find out what these differences are.
Lydia - Absolutely. There are a lot of other things that we can do as well. So, my team is looking at putting interventions in that support medical staff to help them make a system safer. We're looking at the epidemiology of people. If we can connect up all the medical records in a country like the UK with the NHS, what we can do is actually look from birth to death at what the risk factors are for each and every individual problem.
Chris - What about the one thing that people often do highlight with medical records and their personal data, the safety of that data, the integrity of that data, making sure it doesn't get hacked for example?
Lydia - I think that's a really important question and I think it's really important to share how we do that and the first being that in the UK, we have two datacentres that are to the highest NHS standards dedicated to hold this information. It is not accessible on the internet as you well know maybe being a doctor trying to look it up on call....
Chris - Allegedly, I can access this from home and I've tried and it told me I wasn't allowed.
Lydia - That's because you're not quite fitting into the security system. If you go talk to IT, they'll help you out with that.
Chris - That's kind of a good test I suppose. If its own staff can't get in, that's kind of proving that the data is secure, isn't it?
Lydia - Well, I think we want the doctors to have access to the data, but the other thing that I should highlight is that EPIC, which is the system that we bought, has been running for over 20 years in the US in multiple systems and around the world, and there has never been an external breach of the system. So, I think people should feel quite secure in that. If they don't then I can tell you what the data look like on the back end. There's no nice spreadsheet where Mrs Smith and all the details next to it. Connecting that up takes a lot of computer programming and as you well know on the front end, in order to get in, you have to have a medical log in which we can monitor and we can see everything you're doing. Not to scare you Chris. And then you have to have specific details about the patient such as their medical record number, their birth date. You can't just look people up by their name.
Chris - You say that this is the first time this has been done in the UK which is a big step forward for the UK, but compared with other countries, how do we fare?
Lydia - Compared with most high income countries, we are a bit behind in terms of getting medical records electronic and out there. That's because it's been recognised as an opportunity for high quality patient care and safety. And so, what we're trying to do now and what the Department of Health has called for, sometime between 2018 and 2020 to have all medical systems on an electronic medical record.

42:58 - The data you give away online
The data you give away online
with Dr Richard Mortier, University of Cambridge
Every time you go online you are providing information: your clicking and shopping habits and preferences. But how is this data used and who is using it? Richard Mortier works for the Computer Laboratory at the University of Cambridge, and has been peering behind the curtain of this digital tracking, as he explained to Kat Arney...
habits and preferences. But how is this data used and who is using it? Richard Mortier works for the Computer Laboratory at the University of Cambridge, and has been peering behind the curtain of this digital tracking, as he explained to Kat Arney...
Richard - A very common case for example is, just as you're browsing websites, you'll find that most websites, when you pull them to your browser and the browser shows them to you are running pieces of code in the background. Those pieces code are pulling other information in from other websites to show you advertising. Maybe they send back analytics and statistics about who's doing things. As you start to stitch together some of the sites that you visit, they'll be using many of the same ad tracking networks and the same systems. And so, some of these systems are able to start stitching together a picture of where you visited on the web and what your interests are as a result. I think the concern is not so much that advertising is a bad thing because it can be a good thing. Although it can have surprising side effects. There's one case of a teenager in America who was sent some advertising tool from a supermarket chain called Target and the material was to do with items that they wished to buy them to do with being pregnant. Her father didn't know that she was pregnant and so, gave the supermarket manager apparently an info about it and had to apologize a few days later because it turned out that she was. And so, it became something as a surprise to them. So, even with just simple advertising, it can sometimes be surprising what behaviour is revealed through this. It's often revealed in a way that you can't control, you don't anticipate, and you don't understand.
Kat - I mean, that's my next question. When I go online, say if people are going, okay, you've bought this, you've got that. It looks like you're going on holiday to Bradford which is where I'm going soon. How long is this information stored for and what sort of companies are we talking about storing it?
Richard - I think that's part of the problem is, that it's not entirely clear to the people who the information concerns. So, information is typically going to be stored for a very long time. There are some evidence that for example, Facebook is starting to show you things in your timeline from several years previously and in many people's cases this came as an unwelcoming surprise. They saw evidence of relationships that had long since finished for example. It can be stored for a long time and it can be shared and used in ways that are not always made obvious to you.
Kat - We're going to have a quick look at a website now. I mean, what sort of things are we talking about here? Is there any way to find out who is looking at my data? Let's have a look what we've got here. We've got a newspaper website.
Richard - So, in this web browser, I've installed a couple of plug-ins that allow you to see some of these transactions taking place. So, if for example, I reload this web page, it's a popular Sunday newspaper.
Kat - Other popular Sunday newspapers are available...
Richard - Indeed. We'll see some information popping up shortly on the right hand side of the screen. So, you can see the number of sites that are being blocked here.
Kat - 36...
Richard - 38, I think now, 47, 60. So, there's many, many sites are being contacted as a result of having loaded just this front page of this particular website.
Kat - Okay. This is just one page of a website and there's now - we're up to like 60 websites. Are these all just advertisers, just trying to get hold of my data?
Richard - Some of them will be advertising, some will be analytics, some might be - there's a Facebook site in there, there's Google page in there. So, there's a variety of different companies that are being contacted. None of which was necessarily obvious to anybody just visiting this page.
Kat - I've not heard of most of those companies. How can I stop them finding out about my stuff? I don't want all these unpronounceable companies looking at my data.
Richard - So, you can do that by installing some - commonly, you install things into browsers or you use private browsing mode and so on. It can become a little bit intrusive because you start to find that bits of the experience you expect on the web stop working when you start blocking all of these for example. Another one, a plug-in that's showing here is showing the linkages between some of these advertising sites. So, the fact that you go to two completely separate websites there, you visited 2 sites. It's telling me that it's being connected with 108 other sites as a result and some of those sites are shared between the two sites actually visited. So, you can start to see some of the linkages that it created in this ecosystem.
Kat - Now, that could be concerning if you don't really want one website know another website thinks of you.
Richard - For example, yeah. I think it gets even worse when you start to throw other things in the mix. So, some of the ability for example of Google with all the Gmail accounts that people have to scan the contents of your email and see some of that. If you're sending your Ocado shopping online receipts to a Gmail account then all that information is in there as well. So, there's a lot of information that you put out out there and without necessarily understanding the implications of all these different companies having access to some of it or being able to pull it together in different ways.
Kat - Is there anything that people can do? You've mentioned some blockers and things like that. If you don't want people to see what you're up to online or track your data, is there much awareness that people can block this?
Richard - I think well, there are certainly blockers out there that you can install into a number of the common browsers. I know some people or some colleagues for example would go to the extent of not having mobile phones so they can't be tracked because they believe...
Kat - That's their excuse.
Richard - There's a spectrum of responses you can have to this. Some people just don't care. Maybe they don't see they need to. I think the key thing here is to get a sort of understanding and start to see some of this revealed a bit more so we understand it and respond to it more appropriately.
Kat - I was going to say, is there any kind of regulation of this? 108 third party websites have seen the two sites that we've just taken a look at. Does anyone know about that? Is anyone overseeing this? I assume they're not just UK sites.
Richard - No. There is a regulation that applies to this. It's not an area I'm particularly expert in, but certainly, the European Union and the Data Protection Act for example that has been applied in the UK as a result of their legislation in the EU tries to control how some of these information has to be treated - what can be done to, what can't be done to. But there's a constant sort of evolution here where the technology moves quickly and lawmakers try and keep up with it essentially. So, I think it's quite an active area at the moment. It's evolving quite quickly.
Kat - Very briefly, what do you see as the future of this? I mean, in a good light.
Richard - I think that it's about giving people, the people who want to, the knobs that they can turn in order to control this experience, and allowing people to share what they want to share and not to share what they don't want to share. At the moment, it's just happening outside of your control essentially and so, there's really too much going on without you being aware of it. Ideally, it would be up to you to make decisions about what you wanted to have happened here. If that meant that you didn't care and you wanted everybody to see everything you did, that would be fine. And if you've meant that you wanted to hide everything, that would be okay too.

49:20 - The dangers of public Wi-Fi
The dangers of public Wi-Fi
with James Lyne, Sophos
Your home internet may be secure, but do you ever connect to Wi-Fi? If so, you  might want to take extra care to look at exactly who you are connecting to. Jame Lyne is head of security research at Sophos, a digital security company, and has been very busy looking into the worrying Wi-Fi habits of the public, as he explained to Chris Smith...
might want to take extra care to look at exactly who you are connecting to. Jame Lyne is head of security research at Sophos, a digital security company, and has been very busy looking into the worrying Wi-Fi habits of the public, as he explained to Chris Smith...
James - There's a myriad of different attacks that occur on wireless networks but the one that we were most interested in was really, people's natural behaviours, their level of trust for just connecting to a wireless network. So, we set up eight or nine different wireless networks and for a period of two hours, walked around, offering people free Wi-Fi, Wi-Fi where they had to register, and in some cases, Wi-Fi where they had to pay.
Chris - Where?
James - Now, this was actually in New York City and I have to say, my most active Wi-Phishing area, as we've dubbed it, was the airport. It seems like people get off planes and are very hungry for wireless to check their emails. In just under 2 hours, we're able to snare 109 people into handing over their credit card details to a company that had as much trust as well anyone on the internet. I bought the logo from a clipart site for about 5 US dollars. The domain name costs another $15 and I bought an SSL certificate, which gives you that little padlock that we're all trained to trust. That was about 50 UD dollars. So, a high trust operation.
Chris - So, let's just explain what you mean by this. You went to the airport or some places around New York. You set up like a Wi-Fi offering, "Connect to me. I'm offering you Wi-Fi" and it would allow people to connect to it to get an internet access and it even offered them a trustworthy looking padlock so they thought they were doing secure internet browsing.
James - That's perfectly correct. We even actually went into the trouble of putting up an end-user license agreement. When you go to a coffee shop, it pops up and says, "Would you like to get online?" you've got that little agreement you have to scroll down. What was really fun was, in the agreement on paragraph two, it says, "This is a Sophos research project. You agree we can monitor your system entirely, log all of your data, and that we may contact you in the future to figure out why did something so stupid." And no one reads it because the average time to click agree was 1.3 seconds.
Chris - So, they all agreed. They connected to your hotspot and invisibly to them you were sitting like the mad in the middle, listening or effectively eavesdropping on everything that they did online.
James - Well, exactly. Here's the thing. When you connect to wireless network, you handover authority of where your computer is going to go on the internet to that network. In my case, the malicious attacker. So, if you ask for a resource like that nice news page we were just looking at, it's very easy for me to redirect you off to a nasty copy that asks for information or maybe delivers some nasty malicious codes that gives me more access to your computer. And there are some mitigating technologies in practices to this but less than 1% of the people connecting actually took those.
Chris - Didn't you do something like, call it, 'do not connect to me' or something and people even didn't fall for that? They still connected to it.
James - Yeah, that was one of my personal favourites. Get online and free public Wi-Fi were very popular, but in capitals, DO NOT CONNECT saw 27 visitors and I envisage these people sitting in coffee shops going, "Challenge accepted."
Chris - When they did connect, what did they do?
James - A mass of different things. Social media updates were of course very popular. We did see a little bit of internet banking. The good news is, most of that was actually encrypted by default so we couldn't poke inside it. There are few kind of nastier techniques we could've used but we're obviously doing this ethically. Of course, all the other websites they visited and there was lots of - in some cases, very strange web browsing. I'm looking to releasing that list at some point.
Chris - Was this in New York or elsewhere?
James - This was in New York although I have to say, we have done a series of Wi-Fi experiments in other locations. So far, Las Vegas has been the one that's caused the most sleepless nights. When you go through that list, of course, any of those unencrypted sites could be targeted and once you've been compromised, your banking details are no longer safe. So, it only takes one kind of weak point in the chain to get you infected.
Chris - In other words, people connect trusting your connection, but you could be inserting data onto their computer that then compromises their computer, so that next time they do online banking, regardless of whether it's got a secure connection to the bank, it's still sending you all the data in the meantime.
James - Precisely and the nasty bit of this experiment that would've been trivial to do, but we stop short off for ethics purposes was to download that malicious code. At which point, you could not only access internet banking, you can access the webcam, you can record from the microphone, and consider - I mean, there are a large number of laptops or smartphones there too. I mean, there are over 1.6 million malicious applications for android devices now. I challenge listeners to think about a time where they don't have their phone next to them. Now, they're making waterproof devices that's getting even slimmer and how compromising that could be to you. We are handing over the keys to our physical lives to cyber riminals in the digital world.
Chris - And you can just plant data onto these devices and then basically, you own them.
James - Well, the good news is, if you follow some fairly simply practices, it makes it a lot harder for cybercriminals. As I say unfortunately, most people are not doing that, but little things like keeping your software up to date, making sure you update your browser. Running good endpoint security.
Although best of all, if you're out and about, don't connect to a wireless network unless you really know who it belongs to. Maybe consider using data on your phone which is much, much harder to intercept.
Chris - You could easily envisage a scenario where people would come to an event like this one where they see big brands knocking around. So, you could be perched on the edge of a big brand tent or something and you could issue a Wi-Fi hotspot so people think, "That belongs to that big brand. They're trustworthy" and in fact, it's you.
James - The only indicator of trust you have when you first connect to a wireless network is the name and you can set that to anything you want. Now, for legal reasons and lawyers spoiling all my fun, I wasn't allowed to steal other people's brands. Apparently, that's passing off or something like that. And so, I was only able to use these generic names. But 2,000 people connected, 500 of them just handed over email addresses, 109 credit cards. Imagine if I was to park up in a coffee shop or outsider, even an enterprise and setup a network with the same name as their employee network, how many people could potentially been snared? Scary stuff.
We've got way to use to this protocol of connecting to any wireless network that professes to offer free Wi-Fi based on some text that anyone could enter.
Chris - We've got a couple of minutes left so let's just explore one other thing which is getting to be big business. This is the internet of things. Now, you're saying, "Let's keep our devices all up to date" but we're all dependent on third party devices which really probably have quite shoddy security, so we can't really do that.
James - Yeah, that's been another one of my recent research projects. Another one with lots of lawyers involved telling me what I shouldn't do. I've been following the rules.
So actually, I've got a little case here with me which is packed with various internet of things, devices. So, I went on to amazon and we bought about 5,000 pounds worth of CCTV cameras, various other bits and pieces, and went through them to find out how many of them had critical security vulnerabilities. Long story short, all of them did except for one, which actually was so poorly implemented, we couldn't access it, which is what I like to call security through, well essentially, obscurity and unintelligence.









Comments
Add a comment